Salesforce Sharing & Visibility Designer Certification
Recently I’ve cleared the Salesforce Sharing & Visibility Designer Certification, my first step towards becoming a Salesforce Technical Architect and so I thought of sharing some insights about the exam. After platform developer II certification, this is undeniably one of the challenging and fantabulous Salesforce exam. Now I have experienced the difference between knowing the path and walking the path, what an amazing experience!!

[Update] : If you preparing for Platform Developer II Certification , please click here.
Salesforce Architect Journey
Salesforce-certified architect credentials comprise three tiers of certification that recognize specialized knowledge and skills, as well as your growing expertise in the Salesforce platform:
- The Salesforce Certified Architecture Designer credentials validate knowledge and expertise in particular specializations.
- The Salesforce Certified Application Architect and System Architect certifications recognize professionals who possess expertise in a domain area.
- The Salesforce Certified Technical Architect (CTA) credential is the pinnacle certification for those who demonstrate the knowledge, skills, and capabilities to design and build high-performance technical solutions on the Salesforce platform across all areas of domain expertise. CTAs are the Salesforce elite – you should aspire to become one.
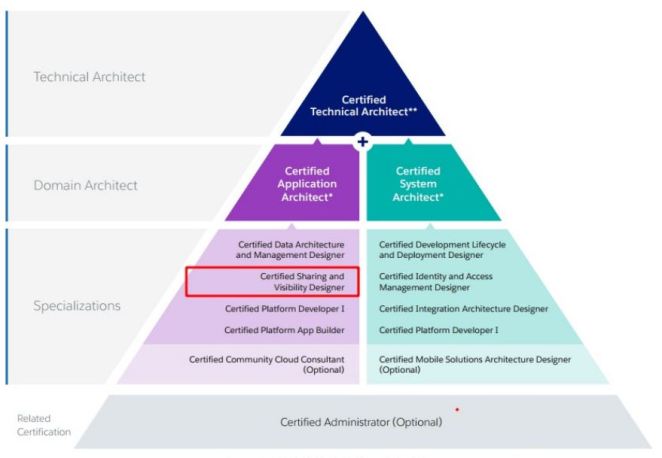
Source: Salesforce University
Audience
As per the Salesforce university – “The Salesforce Certified Sharing and Visibility Designer credential is designed for those who assess the architecture environment and requirements and design sound, scalable, and high-performing technical solutions on the Force.com platform that meet sharing and visibility security requirements. Candidates should have experience communicating solutions and design trade-offs to businesses and IT stakeholders.“
Here is the full outline of the exam.
If you have rich hands-on experience with Profiles, Roles, OWD, Sharing Rules, Salesforce licenses, Permission Sets, Record Locking related issues, Territory Management, Communities, Apex Managed Sharing, Account & Opportunity Teams, then there is a green flag for you.
Force.com is the preeminent cloud application development platform in use today, supporting more than 100,000 organizations and 220,000 deployed apps, so it’s very vital to understand the security and sharing.
Sharing & Visibility blueprint
There are several articles around, but they missed to explain all the nuts and bolts involved with sharing & visibility and how to enforce levels of security when customizing application on force.com platform.
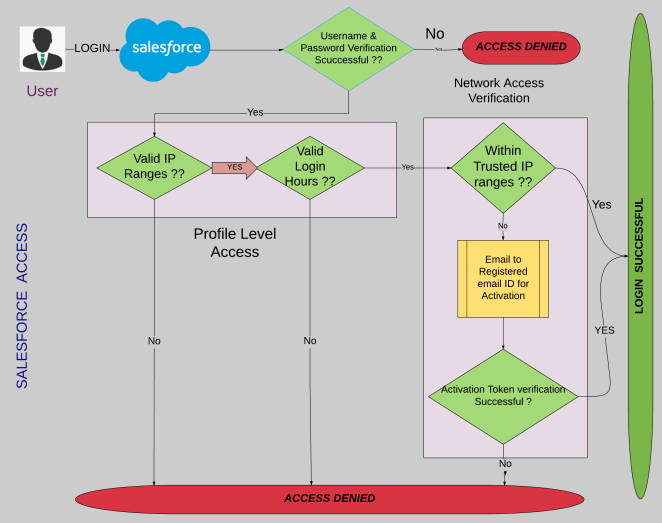
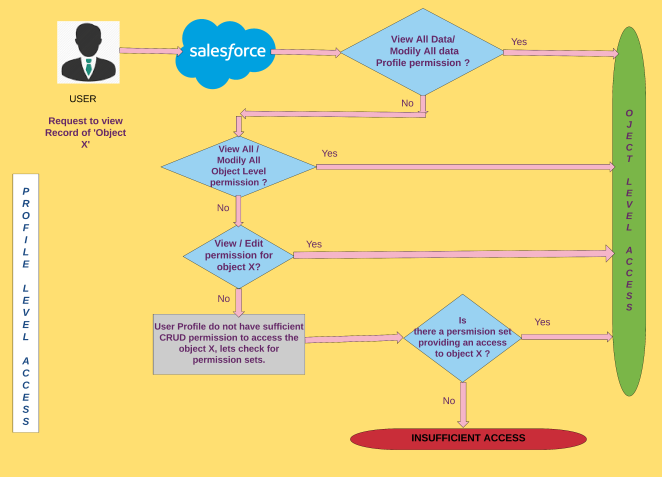
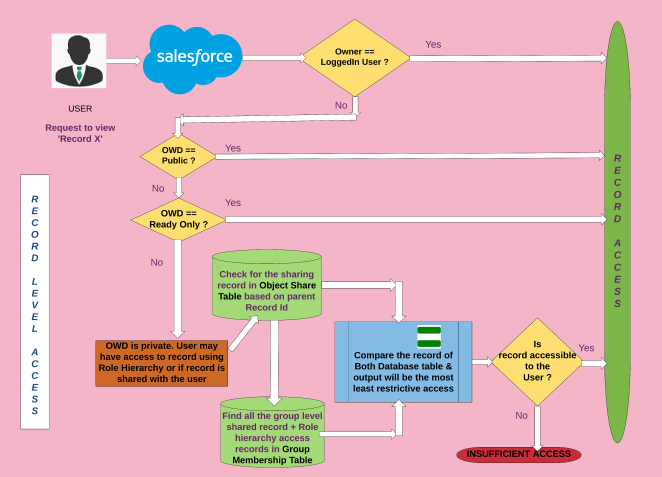
So without further ado… Let us take an example where user wants to access the Object X record on the salesforce org, to get the clear picture I have divided this paradigm to four blueprints listed below,
- ORG Level Access i.e Salesforce Access
- Profile Level Access
- Record Level Access
- Field Level Access
Before moving ahead, I would highly recommend all the readers to go through the Salesforce blog – Salesforce Data Security Model — Explained Visually.
Note: I have considered higher level overview to make flowchart self-explanatory and quite simple to understand.
Now let us understand each of these blueprints one by one,
ORG Level Access i.e Salesforce Access
Profile Level Access
Record Level Access
To have a better overview of the below blueprint I strongly recommend going through Salesforce’s Record-Level Access: Under the Hood Documentation.
Field Level Access
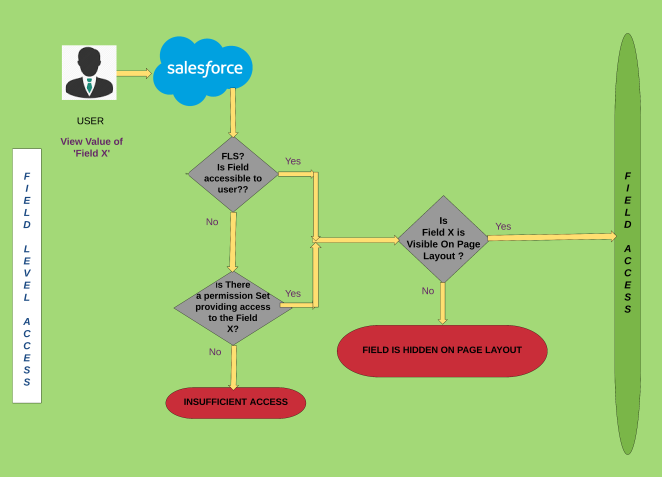
These self-explanatory flowcharts give the higher level overview for an example where the user wants to access the Object X record on the salesforce org. Now let us look at the few other aspects of security.
Cross-Site Scripting (XSS)
Cross-site scripting is a vulnerability that occurs when an attacker can insert unauthorized JavaScript, VBScript, HTML, or other active content into a web page viewed by other users. A malicious script inserted into a page in this manner can hijack the user’s session, submit unauthorized transactions as the user, steal confidential information, or simply deface the page. Cross-site scripting is one of the most serious and most common attacks against web applications today. Read More.
SOQL Injection in Salesforce
As part of Salesforce development best practice, we need to pay very special attention to SOQL injection. Organizations are putting their most trusted information into Salesforce with the understanding that the data is secure. Company financials, customer lists, products, employees are all examples of very sensitive data to a company. As a developer of Salesforce applications, part of your job is to uphold the security put in place by the Force.com platform. A big part of this is making sure that the custom code you write cannot be used to cause any hard to the organizations using your code.
There are a number of techniques you can use to prevent SOQL injection, but to use them depends on what you’re trying to accomplish with your query. Read More
Cross-Site Request Forgery (CSRF)
Web browsers allow GET and POST requests to be made between different websites. Cross-site request forgery (CSRF) occurs when a user visits a malicious web page that makes their browser send requests to your application that the user did not intend. This can be done with the srcattribute of the IMG, IFRAME or other tags and more complicated requests, including POSTs, can be made using JavaScript. Because the browser always sends the relevant cookies when making requests, requests like this appear to originate from an authenticated user. The malicious site isn’t able to see the results of these requests, but if create, update or delete functionality can be triggered, the malicious site may be able to perform unauthorized actions. Read More.
Protips
- Finding an architectural issue can be like finding a needle in a haystack !! So be focused and attentive while reading the question.
- Time is money! Master Your Time, Master Your Life.
- Reverse engineering is the key! Get the right answer by eliminating the wrong one.
Referral material

- Salesforce: Sharing Cheat Sheet
- Territory Management Decision Guide
- Enterprise Territory Management Implementation Guide
- Who Sees What
- Record-Level Access: Under the Hood
- Enforcing CRUD and FLS
- Designing Record Access for Enterprise Scale
- Protecting Force.com Custom Sharing Code
- Behind the Scenes of Record Ownership in Salesforce
- Understanding With Sharing, Without Sharing & Unspecified Sharing Classes
- Shield Platform Encryption
- Using Apex Managed Sharing to Create Custom Record Sharing Logic
- Managing Lookup Skew in Salesforce to Avoid Record Lock Exceptions
- Full Study Material is actually documented by SFDC here
Good luck folks and feel free to tweet me @JitenJoysar if you have any questions! That’s it for this article, See you in next blog.
Stay Happy, Stay Tuned !!
Note: Kindly refrain asking questions, dumps, as I don’t have any and this would also breach the test taker agreement. It’s Self-pride when you clear certification without dumps.
Thank-You Note
I’m humbled and grateful to mohith shrivastava and Matthew Morris for amazing support and guidance.

Awesome. Good information.
LikeLike
I was going through various article for sharing visibility designer certification.
But I must say that yours was most compressive and well explained.
Really you have maintained the interest. Thanks a lot for such article.
LikeLike
Reblogged this on SFDC Panther and commented:
Salesforce Sharing & Visibility Designer Certification
LikeLike